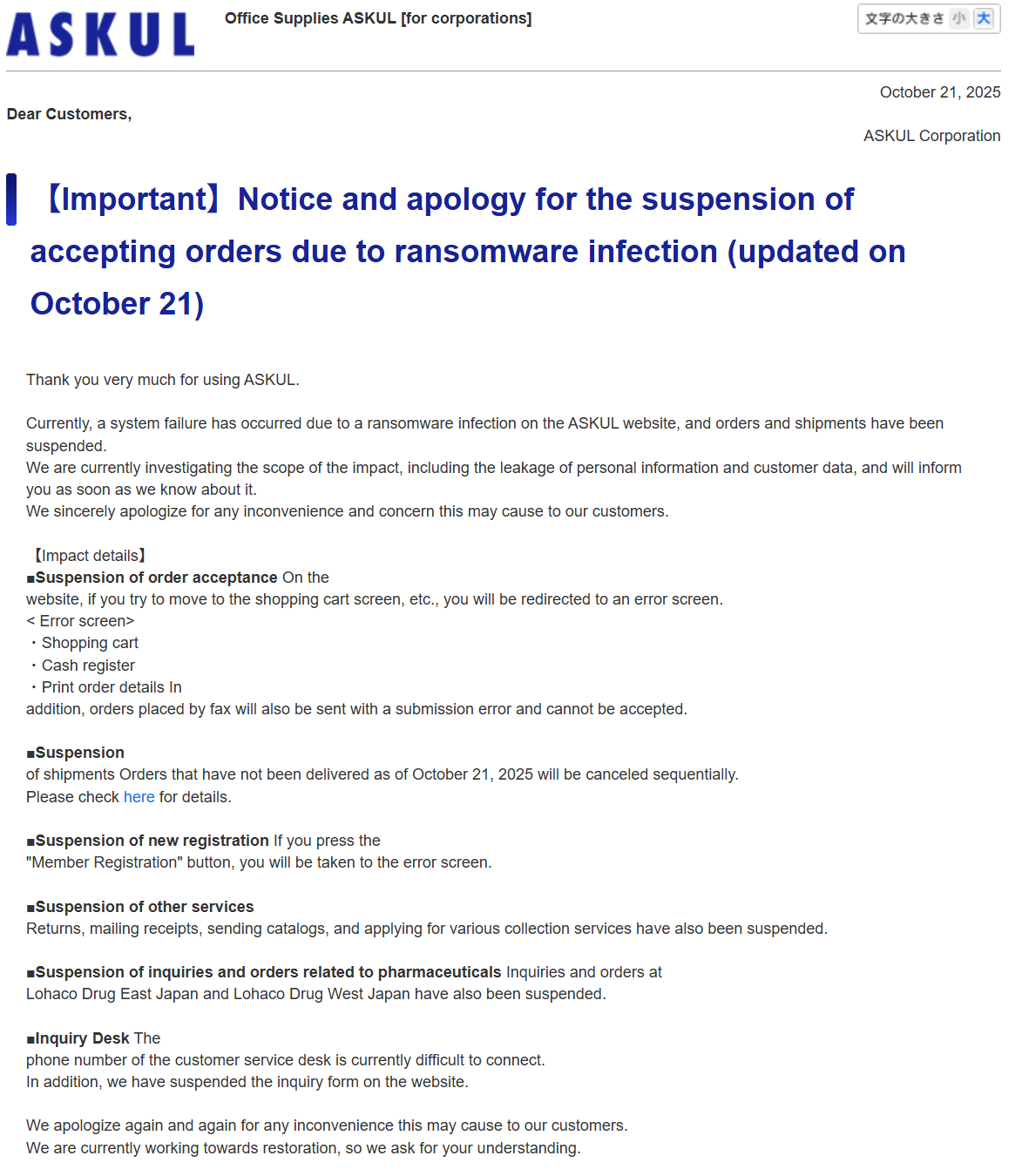
The Update: Askul confirmed on Tuesday that a system failure caused by a ransomware infection had forced it to halt orders, shipments and customer service operations. The company suspended new user registrations, catalogue requests, returns, pharmaceutical orders and customer service hotlines.
Muji announced that these logistics failures had disabled its online store and subscription services, with no timeline for resuming orders. Its parent company, Ryohin Keikaku, stated that its own systems remain secure and physical stores are unaffected, although online operations will stay offline until Askul recovers.
Other retailers, including Loft and Sogo & Seibu, have also reported service disruptions linked to the Askul incident. The company is still investigating whether any customer data has been compromised, and undelivered orders placed before 21 October have been cancelled. No ransomware group has yet claimed responsibility.
This follows a similar attack on Asahi Group Holdings, which was claimed by the Qilin ransomware gang and continues to affect operations.
Why It Matters: The Askul breach highlights how one compromised supplier can disrupt an entire business ecosystem. By targeting a single logistics provider, attackers have paralysed several well-known retailers, showing how ransomware operators exploit supply chain dependencies to amplify damage and leverage extortion.
The financial and operational fallout from such attacks continues to rise. A recent report by cybersecurity firm ExtraHop found that the average ransomware payment in 2025 has increased to $3.6 million, up from $2.5 million last year.
This incident reinforces the need to look beyond internal systems and strengthen the security of their third-party vendors. Continuous monitoring, regular risk assessments and robust incident response plans are essential to reducing exposure. For consumers, the Muji shutdown serves as a reminder that the convenience of online shopping relies on a complex digital infrastructure that can be quickly disrupted by a single breach.